 Comarch Transaction ProtectionProtect your customers from fraud transactions and save on operating costs
Comarch Transaction ProtectionProtect your customers from fraud transactions and save on operating costs

Looking for a cost-effective solution to secure your customers’ logins and transactions? Comarch Transaction Protection (tPro) is what your company needs! Designed for banks and other financial institutions, the tPro suite consists of two innovative solutions for strong customer authentication and transaction authorization: tPro ECC and tPro Mobile.
The first element of the platform is the Comarch tPro ECC solution - a professional hardware cryptographic token, equipped with a proprietary button, the pressing of which initiates the authentication or authorization process. The whole solution is contained in a compact casing the size of a flash drive and connected to the workstation via a USB port.
The second solution is Comarch tPro Mobile - a modern application token, enabling not only secure authorization or authentication, but also allowing for the integration of cryptographic tokens of various applications in one place.
The tPro platform uses advanced technology, strongly focused on cyber security. Both the elliptical curve cryptography (ECC) and the adopted architectural solutions used provide protection against multiple attack vectors, such as password stealing, identity theft or man-in-the-middle/browser attacks.
The tPro solution family can be used for a variety of purposes. The most intuitive and popular use cases for tPro are:
Proactive security features designed to increase customer protection during login and transaction authorization
Driverless approach providing full OS and browser coverage without the installation of any additional hardware, software or middleware to buy, deploy and maintain
Possibility of integration with the tPro Authentication Server, a module of Comarch Identity and Access Management (IAM) expandable with additional features
Full control over R&D and production allowing for easy customization of both hardware and software in response to different market demands
Comarch tPro Mobile is more than just a 2 Factor Authentication (2FA) tool. There are also other applications for the tPro family which, especially during the period of widespread remote working, can be used extensively. It ensures a secure VPN connection and supports remote work. The geolocation feature lets you verify where your employees are. You can also sign documents remotely. All that with the highest level of security available.
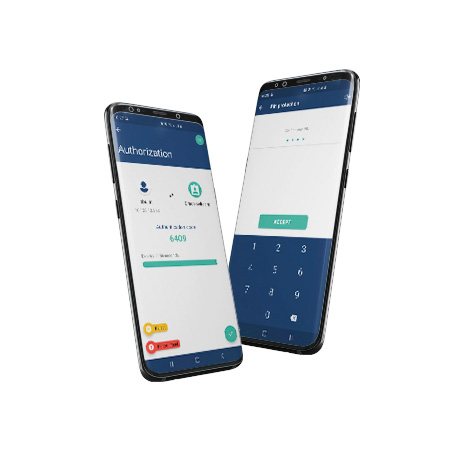
One such solution is to use tPro Mobile as a VPN (Virtual Private Network) authentication token.
As the tPro platform is based on strong encryption of transmitted messages, it can be effectively used as an authentication tool, integrated with network devices, to implement VPNs. With this solution, the access to corporate resources is secure and the user identities are protected from attacks. The offered solution is also convenient and user-friendly. This is ensured not only by a friendly interface, the use of biometrics or PUSH technology, but also by a simple onboarding process based on QR codes.
The conducted stress-tests have shown that the solution effectively carries out VPN authentication based on OTP codes (HOTP, TOTP), ensuring the efficiency at a minimum of 50 queries per second.
Another possible application of the tPro platform is the determination of user geolocation. This is done on the basis of coordinates from the GPS and network IP. The verification of a user's geographical location may be necessary to ensure their security: to be able to protect a person, it is necessary to be sure of their physical location. Geolocation can also be used to protect classified information. Based on local legislation or the security policy of the company, it may be prohibited to use specific data outside the company's headquarters or outside a certain area (e.g. abroad). Locating a user outside the nominal access area may result in the denial or restriction of access to specific data.
Another feature of the tPro product family is the massive online signing of PDF documents. For all companies and institutions that send electronic documents en masse, the key issue is their reliability. Signing documents sent in bulk (such as invoices or business contracts) should provide a security guarantee that both the sender and recipient have no doubt that the integrity of the message has been fully preserved. Moreover, the sending process itself should be fast and secure. All this is offered by tPro in a service called Document Signer. The solution allows you to sign hundreds of PDF documents in a second. At the same time, it uses electronic seal technology to sign PDF documents in PAdES format to confirm that a particular document has been sent by a particular company.









Proactive security features designed to increase customer protection during login and transaction authorization
Driverless approach providing full OS and browser coverage without the installation of any additional hardware, software or middleware to buy, deploy and maintain
Possibility of integration with the tPro Authentication Server, a module of Comarch Identity and Access Management (IAM) expandable with additional features
Full control over R&D and production allowing for easy customization of both hardware and software in response to different market demands
Watch Comarch presentation on Virtual Non-Financial Risk Summit 2020 and learn more about mobile security measures to protect against fraudulent activity on smartphones and desktops.
Did you know that your mobile might be used as a security tool? Hear our (ISC)2 webinar recorded by Comarch experts and find out how to make authentication mechanisms easier & more efficient.
Download now!Interested in reselling tPro solutions on your local market? Comarch offers distributors and system integrators free access to:
Contact us to learn more about the tPro Partner Program and its benefits!
Tools and features designed for efficient customer acquisition, policy offering and sales
Mechanisms focused on the ongoing policy portfolio review, maintenance and support
Prospect and customer book with quick data access for efficient service and communication
Key claim functionality for servicing agents and customers requesting agent’s claim assistance
Tools for work self-planning, reminder management and task handling
Predefined reports on various aspects of user performance for self-monitoring and analysis
Knowledge base for editor management to share corporate information and documents
Access for business administrators to manage the application

Download tPro Solutions leaflet
Read more about how to protect your customers from internet frauds
Tell us about your business needs. We will find the perfect solution.